How long can your business survive without IT infrastructure and systems?
Most of us do not want to confront this question let alone the situation. However, on the 3rd of June over 10,000 businesses in Australia were confronted with the loss of their IT systems. (estimate provided by CERT Australia). This incident was reported as an AGL email scam – Ransomware. And is just on the back of the AustPost email scam in mid May. Unfortunately, some of our clients were attacked by this ransomware scam –prompting us to send out alerts and report on methods of avoiding these type of scams in the future.
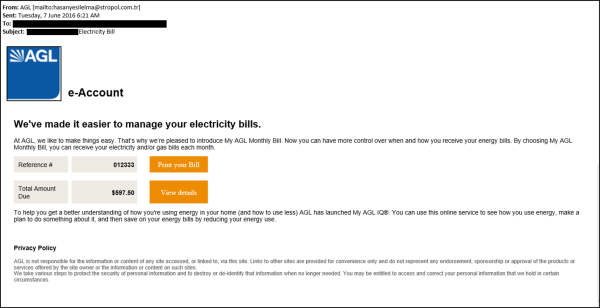
So what is Ransomware? Ransomware is also commonly referred to as CryptoLocker. Ransomware / CryptoLocker is a type of software which restricts access to a victim computer system/device/network and demands a ransom be paid to the perpetrator in order for the restriction to be removed. See the main image - screen shot of the recent AGL scam.
CryptoLocker encrypts documents, photos, databases and certificate files, and then demands payment of an amount in the vicinity of $300. In the case of this malware, the files are encrypted using public key cryptography, so the key is never stored on the machine, and thus is not available for acquisition using file recovery or other forensic techniques.

We do not recommend you pay any fees to decrypt or fee to any unknown third party providers recommended in subsequent emails as these emails are usually from the same scammers.
What to do to prevent future Problems?
Both CERT Australia, ACCC and several software manufacturers have detailed solutions - I have listed some important links below for further reference.
Our 3 golden rules are;
1. Always have an offline backup – “offline” means not connected to any device or network – ie a external hard disk that you take home at the end of the day. (and a tested back up procedure that works).
2. Do not click on links or download files in emails you receive out of the blue — especially if they are executable (.exe) files or zip files. These files are likely to contain malware.
3. Use an upto date virus scan software/firewall that implements application whitelisting or, at least, software restriction policies to hinder the ability of malicious software to execute successfully.
Important Links
- https://www.cyber.gov.au/about-us/view-all-content/alerts-and-advisories
- http://www.scamwatch.gov.au
- https://nakedsecurity.sophos.com/2013/10/12/destructive-malware-cryptolocker-on-the-loose/
Security is a massive issue for all of us now. Our endpoint security is vitally important, but common sense is the valuable tool to mitigate against these sorts of scams. Exercise care and common sense.
Many businesses are still running old sites and outdated site security – we offer maintenance and upgrade services for old websites and web based apps – Please call us on 03 9899 3100 to get help today.



